Some of our customers may want to see our billing policy. So, we’ve decided to publish here to make it easy for customers, and prospects, to access it.
The Computer Guys LLC Billing Policy 2017
Billing: A necessary evil in our profession. The fact is, we enjoy our work and interaction with our clients, and, if we could, might be quite content doing our work for free. We can’t, so we send you bills for the work we perform. We bill for the time we devote to serving your needs. Like your doctor, we don’t bill for the results of our work; we bill for our work. Sometimes we have to expend time finding out what is wrong, what might work, what won’t work, or trying things that don’t work in order to find out what will work. We necessarily bill for that kind of time.
Research: Sometimes we have to consult with our associates internally, or with support staff in companies that have supplied products you are using. Sometimes we have to spend time researching details that relate to your system. For most problems, we should know how to find the resolution to the problem in a reasonable period of time. We don’t, and you should not, expect our staff to answer every question or resolve every problem immediately or without any research. If the best method for finding that resolution is for one of our technicians to review the problem with another of our technicians, or to review it with the maker of the product, we make no apologies and we necessarily bill for the time required. The old story about the washing machine repairman comes to mind. The customer complained about the repairman’s $100 bill. After all, the customer complained, all he did was tighten one screw. The repairman then rewrote the bill: Tightening screw to resolve the problem – $1.00; knowing which screw to tighten – $99.00.
Experiments: Sometimes the best method of resolving a problem is to implement what, based on our experience and research, we think will resolve the problem, let you test the result in your real-life work for several hours or days, and then return if needed to refine the solution. Returning to refine a solution does not constitute failure or reduce the value of previous work we have done.
Malicious Software Resolution: This can be particularly complex. By design, viruses & other malicious software hide, replicate, transport, and recur. Virus resolution almost always requires at least two sessions for success, and even then can easily recur in the near or distant future.
Hourly Rates: Our rates are set to reflect our costs in providing service to you, and in the hope, of course, of earning a reasonable profit. The rates we charge vary depending on the type of service we are performing for you since that most directly affects our cost. Database & Engineering services are charged at higher rates than PC Technician services. Phone support will be billed at regular rates.
Travel time: For short distances from our office or current location to yours is simply included in the time we bill for our work. Also, mileage will be charged if when traveling outside the Wendell Ford Expressway or anytime we are traveling on your behalf, to purchase stuff for your specific location.
Discounts: We sometimes discount our rates. If we are doing a particularly large project for you or if you are located in certain geographic regions, we may apply a small discount to our rates. These discounts are subject to receiving payment within the terms we specify on our bills. If you fail to adhere to these payment terms we will reapply to your account any discounts we may have applied.
“Out-of-Pocket” costs: These are costs that we incur on your behalf. In many cases, these costs are for software or hardware that we provide. These items are billed to you with NO markup and are considered a “Reimbursable Expense.” Because there are additional costs associated with providing these items, we normally apply billing time but no markup on the items themselves. We work hard to find suppliers that can provide us with the highest quality hardware and software, not necessarily the lowest cost so you may be able to find comparable items (or at least what appear to be comparable items) at a lower cost elsewhere. We do not provide warranty service for any hardware or software problems since we do not manufacture or produce hardware or software. Most of the items that we provide include a manufacturer’s warranty. These warranties cover repair or replacement of a failed item, but do not usually cover our time in diagnosing, shipping, replacing or otherwise affecting the warranty. Like warranties of other products, these warranties cover the item’s failure, not associated costs or inconvenience. We will be happy to assist you in contacting the manufacturer yourself in order to reduce our charges in working on warranty issues.
Billing Frequency: Our bills are generated weekly as a project progresses. We expect you to pay out of pocket costs (including travel costs) and costs for proposed projects in advance. If we don’t collect out-of-pocket costs or proposed project costs in advance, they are due immediately upon billing and become past due 5 days after the billing date. Unless specific credit terms have been requested and approved in writing, charges for routine services are due when billed, and become past due 15 days after the billing date. We will usually perform routine and occasional service for established clients and bill for the service after it is complete. New clients, those for whom we do little or irregular service, or clients with whom we have experienced past credit problems will be required to make a deposit payment before work begins. We will estimate the cost for work to be performed and will base the deposit payment on that estimate. We may need to revise our estimate and receive additional deposit payments during the course of a project. Deposit payments will be applied as a payment to your account, and will be reconciled in our regular billing process. We will process a refund of excess deposit payments if needed.
Past-due Amounts: Like any business, past due accounts are a concern for us, and we apply strict procedures in dealing with them. We would prefer to never apply finance charges, and we think you will find our finance charge procedures quite liberal. But if we do apply a finance charge, we are not easily persuaded to reverse it. If your account is past due, you will find that we rarely apply any write-down at all, and if you question a charge on your bill, we will not write it off until the account is brought to “current” status. If we do choose to reverse charges that have been applied to an account that was past due and has since been brought to “current” status, we will only do so in the form of a credit on the account that can be applied to future services.
Questions: We welcome the opportunity of discussing billing and any other questions with you. Communicating with clients is always a pleasure for us, and we encourage it. Client communication sometimes reminds us of little Jimmy who, at three years of age had not spoken a word. His concerned parents sought diagnoses from the best doctors, who could find no problem. At age five, Jimmy still had not spoken, and extensive medical tests sought out by his anxious parents could still not identify a reason. At age nine, during the family dinner one evening, Jimmy suddenly said, “These peas are cold!” His shocked parents sprang to their feet and excitedly asked, “Jimmy, you’re nine years old; you have never spoken until now. Why!?” “Well,” Jimmy replied, “everything’s been OK up to now.” We are always anxious to hear from you. Please feel free to call us anytime.
Hourly Rates as of January 2017:
Business and Networking: $90
Residential and Not-For-Profits: $65
Engineering: $125
Custom Programming: $100
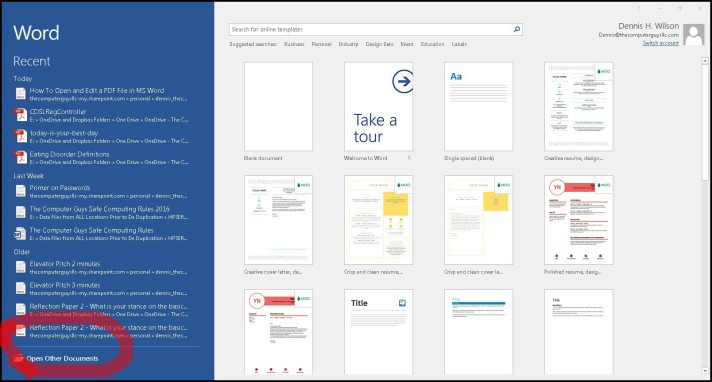
 Word as though you will be starting a new document. In the screen shot below you will notice a list of “Recent” documents. Take note that there are some PDF’s listed. You will not see any PDF’s in your list if you have not OPENED a PDF in Word before. Look toward the bottom of the “Recent” documents list.
Word as though you will be starting a new document. In the screen shot below you will notice a list of “Recent” documents. Take note that there are some PDF’s listed. You will not see any PDF’s in your list if you have not OPENED a PDF in Word before. Look toward the bottom of the “Recent” documents list.